How to Trace Bitcoin Cryptocurrency Address?

If no name, phone number or address is attached to a Bitcoin Public Key, can it actually be linked to a specific individual? The answer is an unsettling and a resounding “Yes”.
Bitcoin has often been mistakenly defined as an anonymous currency, however this notion could not be farther from the truth. There are a multitude of ways inquisitive eyes can link a Bitcoin Public Key to the identity of a user.
The innocuous use of Bitcoin ATM Cameras

A bitcoin ATM is possibly the most obvious way your identity can be compromised and associated with a Public Key. It should be assumed, for security reasons, that Bitcoin ATM’s possess a camera. The physical appearance of an ATM user will immediately be tied to their public key, timestamped and this information WILL be provided to Law Enforcement on request. Additionally, it should be assumed that the premises hosting the Bitcoin ATM have cameras pointed at the machine to identify potential malicious guests.
Even if Bitcoin was indeed an anonymous currency, the use of cameras would completely nullify the benefits of the technology!
Forensic Analysis
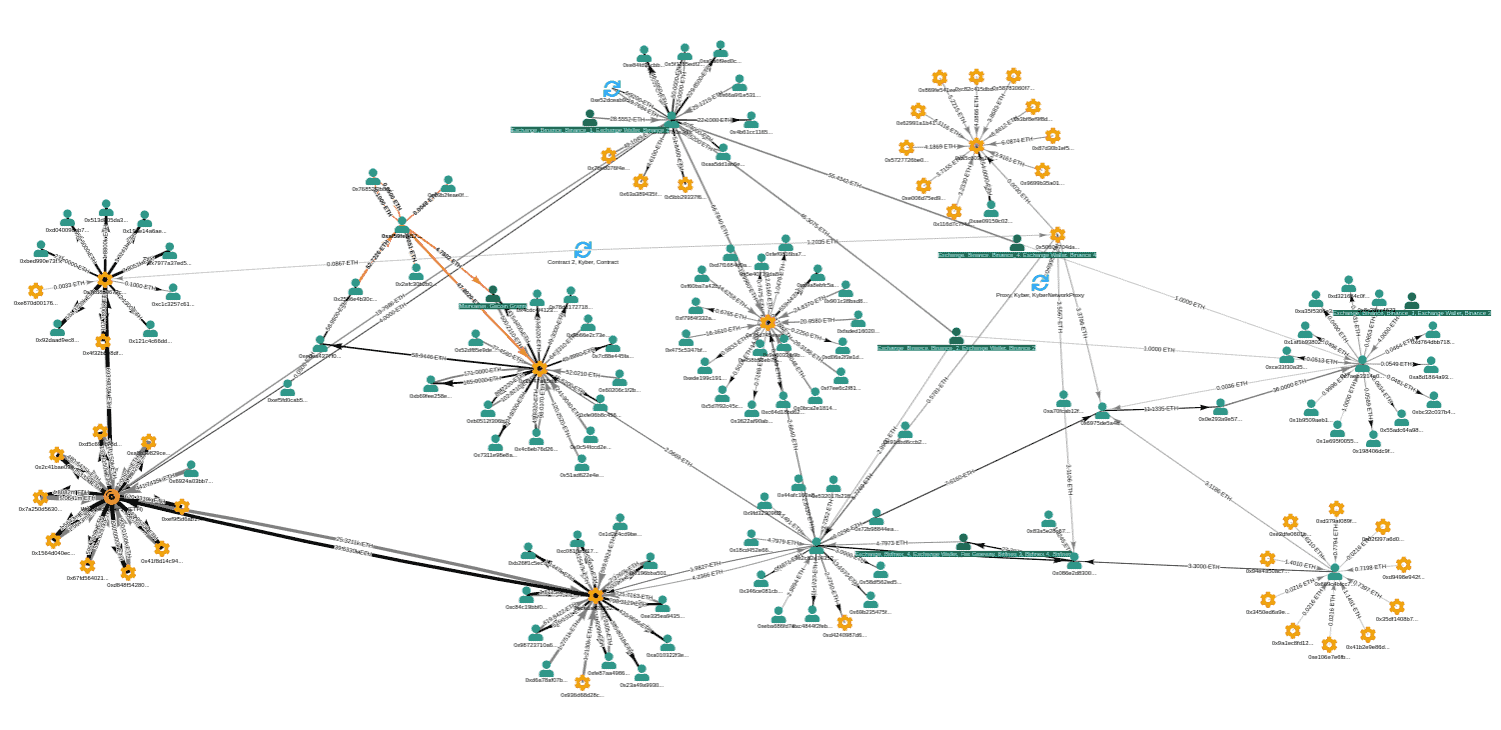
The rapid expansion of the use of Forensic Analysis deals a final blow to this idea that Bitcoin is an anonymous currency that provides a certain level of privacy to its users.
The Chainanalysis KYT (Know Your Transaction) platform, for example, allows users to, astoundingly enough, visualize the flow of funds in real-time. This is a far cry from the manual sleuth work of yesterday. Thanks to this platform it is possible to detect various patterns of risky activity, from darknet markets and outright scams to restricted or sanctioned addresses and anomalous transactions. The Chainanalysis KYT platform is said to cover approximately 90% of all crypto activity. Chainanalysis provides a social media intelligence platform called Reactor that allows users to scan thousands of social media forums (such as reddit, Discord...) using any identifier.
Coinfirm is another forensic firm that provides to businesses and organizations analytics across more than 100 cryptocurrencies and 10 billion data points.
Virtual Asset Service Providers

Virtual asset service providers such as exchanges and custodians are another way to link the identity of users to the public key. Exchanges are routinely asked to provide information about certain users, which they have thanks to Know Your Customer rules that force users who wish to be provided service to disclose their identity first, and to provide government issued identification to confirm their identity.
VASP’s who wish to remain in business and remain in good standing with Governments and Law enforcement agencies are required to comply when issued information requests.
In the face of such technological excellence, what can a lone user do to protect his privacy?

The situation seems hopeless, however there are a few ways individuals hell bent on preserving their privacy can protect themselves.
Let us go over them, starting with the most obvious, to the most complex solutions.
1. Never share your public address on social Media!
Publishing your public key online is never a good idea. It can obviously be linked, by any onlooker, with your social media account. If you have ever shared personal information such as an address or a photo of yourself online, this too will be tied to your public key to form a very compromising portrait. We should be aware of the dangers of sharing things as innocuous as a public key.
2. Change your public key often
If you use the same public key for transfers and purchases, the likeliness of inquisitive eyes associating this key with your online behavior increases dramatically. Maintaining good privacy habits will get you far: change your public key often, discard your Bitcoin wallet after a very large purchase. Changing or at a minimum rotating public keys often will isolate your transactions. A Crypto wallet that allows you to easily generate and manage multiple Bitcoin addresses is highly recommended.
3. Learn to use Bitcoin mixers
A bitcoin mixer, such as Smartmixer, Wasabi Wallet, Bitcoinmix and Samurai Whirlpool, is a service that enhances your privacy by mixing your funds with the funds of other users in order to completely obfuscate the link between your public key and your real-word identity.
There are two different types of mixers, which we will describe below:
A centralized mixer is a service that will accept deposits in Bitcoin and send different tokens in return. The privacy of a mixer is a direct function of the amount of people who use it - just as in the case of Ring Signatures (Monero) in which the more people are part of a specific Ring, the more difficult it becomes to pinpoint the source of funds and associated information. When a lot of people use a mixer service, it becomes rather difficult for an outside observer to link “inputs” (the provenance of funds) to “outputs” (the destination of funds).
A Chaumian Coinjoin mixer allows large groups of people to cooperate in making one large payment to themselves. Let us say that you wish to send 0.1 BTC to an arbitrary address that you own. You send the funds to a coinjoin mixer that will mix your 0.1 with the funds of ten other users each having 0.1 BTC for a total of 1 BTC. At the end of the process, each participant will have sent to an arbitrary address 0.1 BTC, but no one will know exactly where the funds came from!
Wasabi wallet is a popular wallet which offers a Coinjoin service to its users. Wasabi wallet’s infrastructure is centralized, however it is designed so that the owners cannot steal funds or discover the identity of its users.
The Samurai Wallet also offers a Coinjoin service called Whirlpool. Whirlpool has this advantage over Wasabi that it offers a mobile version (Wasabi wallet is desktop only for now). In order to fully take advantage of Whirlpool features, users will need to connect their wallet to their own Bitcoin Full Node.
4. Obfuscate your IP address by using the TOR network.
The Bitcoin network is a peer to peer network and therefore it is possible to listen for transaction relays and log their IP addresses. It is highly recommended to privacy aware users to learn about and use the TOR network. The TOR network is a network of more than seven thousand servers called relays. These relays conceal the location and usage of TOR users from anyone conducting network surveillance and traffic analysis. TOR nodes encrypt and route internet traffic to various other nodes, making it very difficult (but not absolutely impossible) to pinpoint an IP address.
Final Thoughts
As we have seen above, the Bitcoin Network, far from being an anonymous currency, actually exposes the activity of its users on a very Public Ledger. Even if no names, phone numbers or addresses are attached to your transactions, which are visible to all, it is possible to leverage social media intelligence and network analysis, among other things, to link the identity of a user to a public key. There are a number of ways users can protect their privacy. Maintaining good privacy habits, such as changing public keys often or using the TOR network, has become an absolute must!

